Stego-Toolkit - Collection Of Steganography Tools (Helps With CTF Challenges) - Hacking Land - Hack, Crack and Pentest
![Various audio Steganography techniques for audio ijecs.pdf Thus the main purpose of this seminar - [PDF Document] Various audio Steganography techniques for audio ijecs.pdf Thus the main purpose of this seminar - [PDF Document]](https://demo.documents.pub/img/378x509/reader019/reader/2020041110/5b496d4f7f8b9a2d2f8b54d5/r-1.jpg)
Various audio Steganography techniques for audio ijecs.pdf Thus the main purpose of this seminar - [PDF Document]

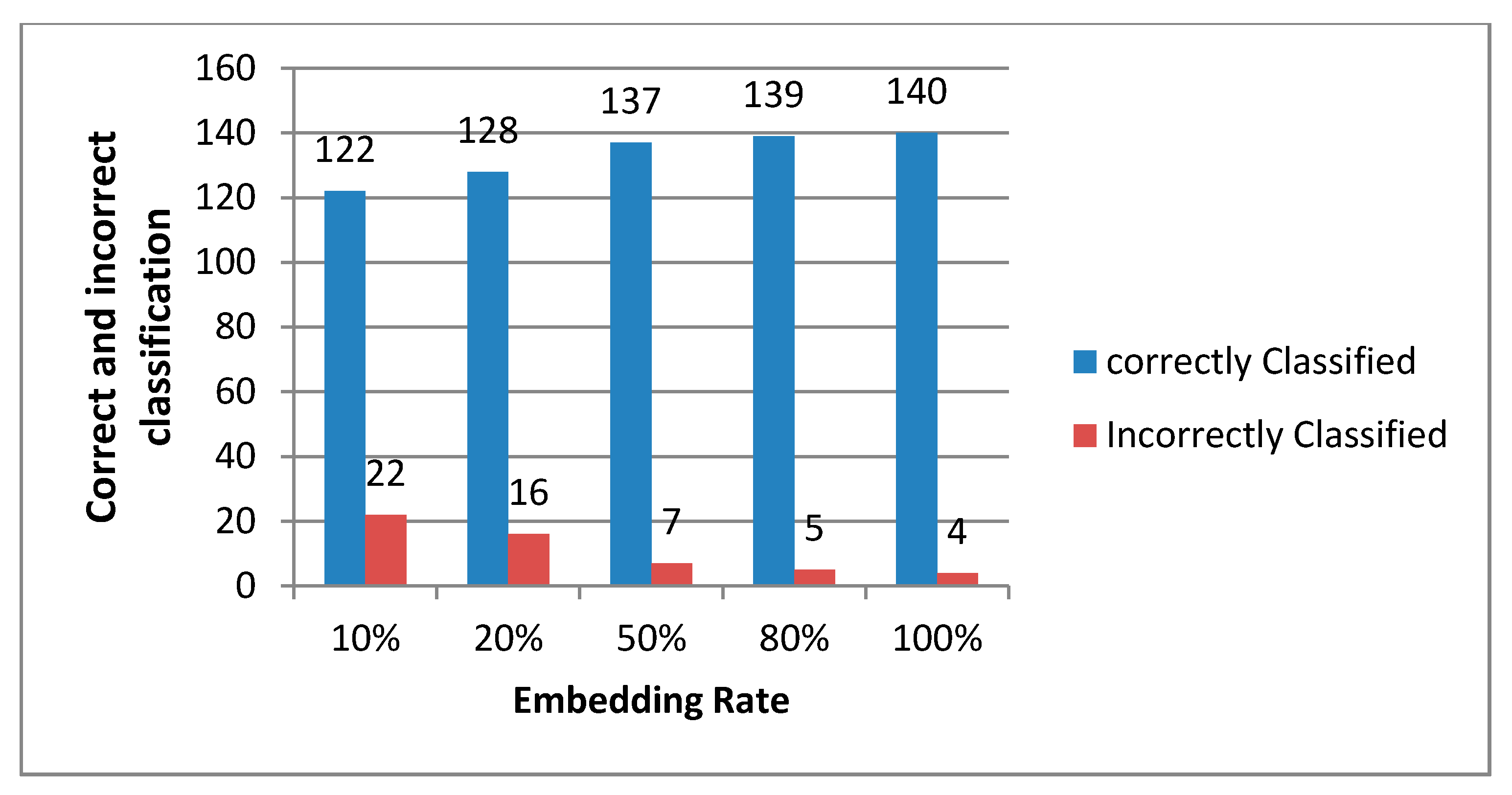
Digital audio steganography: Systematic review, classification, and analysis of the current state of the art - ScienceDirect

Digital audio steganography: Systematic review, classification, and analysis of the current state of the art - ScienceDirect
Audio Steganography via Cloud Services: Integrity Analysis of Hidden File - Document - Gale Academic OneFile
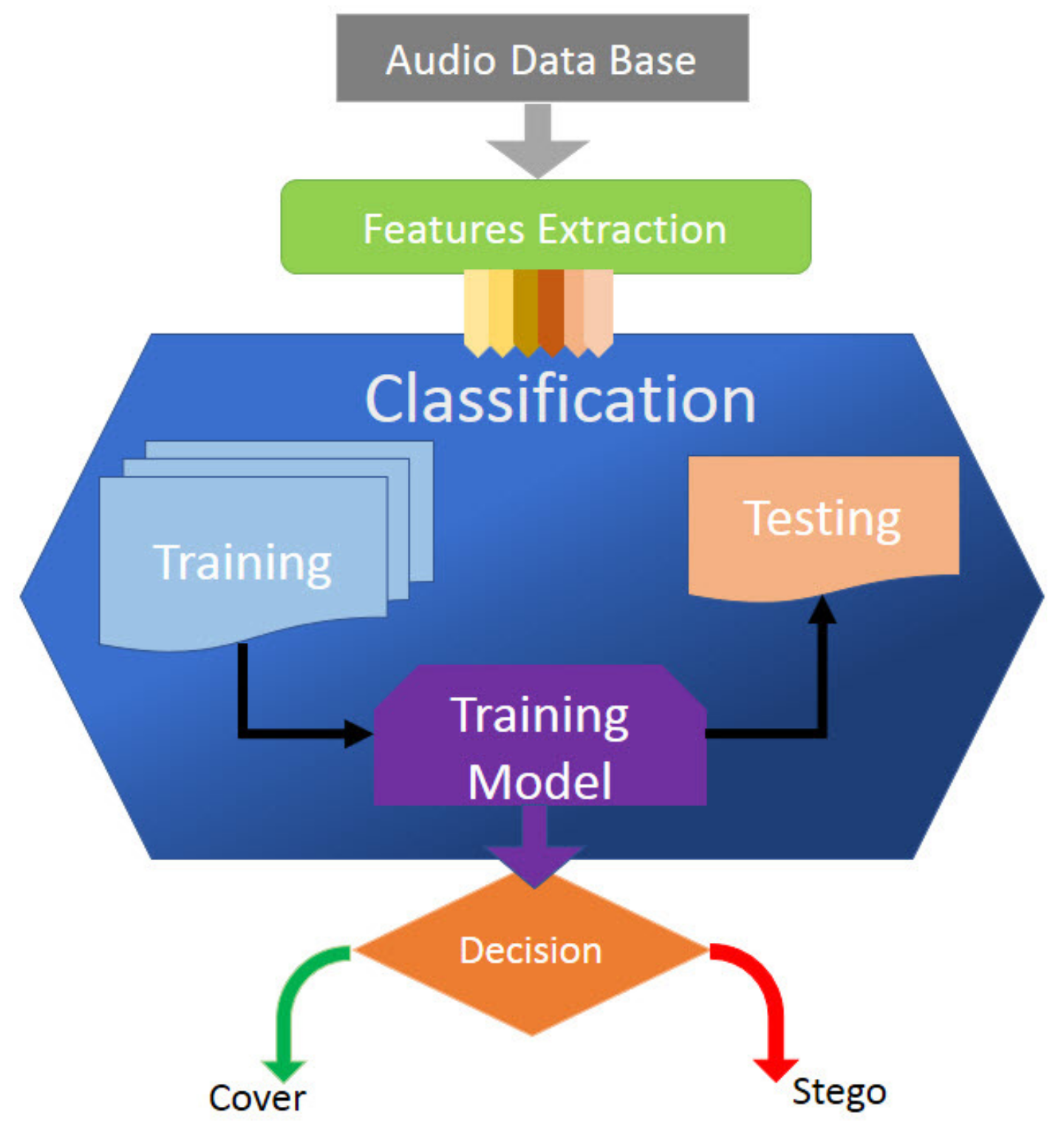
Electronics | Free Full-Text | Securing IoT Data Using Steganography: A Practical Implementation Approach | HTML